Release Notes
orcharhino 6.2 is here!
Highlights
- Running orcharhino on EL8
You can install orcharhino Server or orcharhino Proxies on AlmaLinux 8, Oracle Linux 8, Red Hat Enterprise Linux 8, and Rocky Linux 8.orcharhino contains Kickstart files to provision a system for orcharhino Server. For a complete list of Kickstart files, see Kickstart Requirements in Installing orcharhino Server.
orcharhino is available as Open Virtual Appliance (OVA) image to run orcharhino Server on AlmaLinux 8.With orcharhino 6.2, users can either install orcharhino on EL7 or EL8; or upgrade orcharhino 6.1. to 6.2 without changing the EL version and distribution. With one of the upcoming orcharhino releases, we will provide a way to migrate from EL7 to EL8. - Deploy Kubernetes Clusters with orcharhino
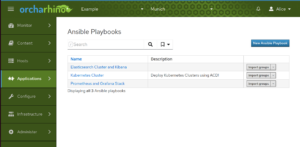
We now provide an Ansible playbook for the Application Centric Deployment (ACD) plug-in to deploy Kubernetes clusters. You can download the Ansible playbook from github.com/ATIX-AG/acd_playbook_for_kubernetes. For more information, see Application Centric Deployment. - Live-patch managed hosts using TuxCare’s KernelCare plug-in
We now provide TuxCare’s KernelCare plug-in for orcharhino as a tech preview. The plug-in improves the usage of KernelCare on hosts managed by orcharhino. You can use it on managed hosts running AlmaLinux, CentOS, Oracle Linux, Red Hat Enterprise Linux, and Rocky Linux. Using KernelCare requires a subscription from tuxcare.com. You can find the documentation for the KernelCare plug-in in the orcharhino documentation under Live-Patching Hosts Using KernelCare. - Accessing OS-specfic documention from orcharhino management UI
We have added an OS-independent landing page to orcharhino Documentation. When you click Documentation on any page in the orcharhino management UI, you can select your operating system and are forwarded to the OS-specific guide. This is especially useful for pages such as Hosts > Installation Media.
orcharhino on EL8
Deploying Kubernetes Cluster using ACD
Changelog Features
- Provisioned hosts running Ubuntu have „phased updates“ disabled by default through their provisioning templates. For more information, see https://docs.orcharhino.com/or/docs/sources/guides/ubuntu/managing_content/managing_errata.html#Disabling_Phased_Updates
- Automated setup of the Salt Reactor integration to upload reports.
- Adjusted the Kickstart files to provision a host for orcharhino to leave sufficient free disk space for backups which rely on LVM snapshots. For more information on adjusting the LVM volume groups on existing systems, see https://atixservice.zendesk.com/hc/de/articles/6990912116252.
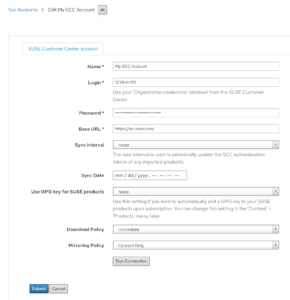
- Added sync options ‚Download Policy‘ and ‚Mirroring Policy‘ for repositories created by the SCC Manager plug-in.
- Added support for Quiesce Snapshots for VMware using the Snapshot Management plug-in.
- Added support for NetIQ LDAP as Authentication Source.
- Added support for Debian/Ubuntu and SLES to the new host registration approach.
- Added several hooks to debian provisioning templates which can be used to add custom provisioning snippets.
- Added new provisioning template for Windows deployment. You can use it to provision hosts running Windows using iPXE over HTTP instead of TFTP.
- Added a host parameter to override the default GRUB kernel parameters on Ubuntu and Debian.
- Added a console (rake) task to identify missing content in subscription management system.
- Added Ansible module to list of all snapshots for a particular host.
SCC manager download policy
Changelog Documentation
- Documented removing the Puppet plug-in from orcharhino Server and orcharhino Proxies. See https://docs.orcharhino.com/or/docs/sources/configuration_management/puppet.html#Disabling_Puppet_Integration_managing-configurations-puppet
- Added documentation on how to register hosts to orcharhino using the Host Registration feature. See https://docs.orcharhino.com/or/docs/sources/guides/rocky_linux/managing_hosts/registering_hosts.html#Registering_Hosts_managing-hosts
- Added documentation on how to use custom pre and post provisioning snippets. See https://docs.orcharhino.com/or/docs/sources/guides/alma_linux/provisioning_hosts/configuring_provisioning_resources.html#Creating_Custom_Provisioning_Snippets_provisioning
- Added a hint to the orcharhino Subscription Key page on how to contact us for subscription-related questions.
- Clarified the importance of setting the correct OS minor version, esp. for Ubuntu 20.04.3+ when using Autoinstall, because orchahrino uses the versions to create the path to the boot files. See https://docs.orcharhino.com/or/docs/sources/guides/ubuntu/provisioning_hosts/configuring_provisioning_resources.html#Creating_an_Operating_System_for_Ubuntu_provisioning
- We have adjusted documentation for registering hosts and running REX jobs on Ubuntu 22.04+ and Debian 11+. See https://docs.orcharhino.com/or/docs/sources/guides/debian/managing_hosts/registering_hosts.html
- Consolidated the compute resource chapter. You can find all supported compute resource provider in the https://docs.orcharhino.com/or/docs/sources/compute_resources.html and in the OS-specific guides, for example https://docs.orcharhino.com/or/docs/sources/guides/debian/provisioning_hosts/ovirt.html
- Added a host parameter hierarchy list to the documentation.
- Updated the procedure on how to update Kickstart repositories for EL 7, 8, and 9. With EL, you can use *synched content* to provision hosts instead of installation media. See https://docs.orcharhino.com/or/docs/sources/guides/red_hat_enterprise_linux/managing_content/managing_custom_file_type_content.html#Importing_Kickstart_Repositories_rhel-9
- Added a hint to orcharhino documentation on how to use local file repositories that are present or created on orcharhino Server. See https://docs.orcharhino.com/or/docs/sources/guides/alma_linux/managing_content/managing_custom_file_type_content.html#Creating_a_Custom_File_Type_Repository_in_a_Local_Directory_content-management
- orcharhino now supports provisioning hosts running Microsoft Windows 11. See https://docs.orcharhino.com/or/docs/sources/guides/deploying_windows_hosts.html
- Added a hint on using external authentication systems to use multi-factor authentication in orcharhino. See https://docs.orcharhino.com/or/docs/sources/guides/administering_orcharhino.html#Configuring_External_Authentication_admin
- Added the free disk space requirements for creating backups using LVM snapshots. See https://docs.orcharhino.com/or/docs/sources/installation_and_maintenance/backing_up_orcharhino.html#Backing_Up_orcharhino_Server_Using_foreman_maintain
- Added a note on updating repositories on orcharhino Server when reverting to a snapshot after a failed upgrade.
Deprecations
- We no longer maintain the orcharhino Client for CentOS Linux 8 due to the CentOS project no longer providing any security updates. Please note that we still support other EL 8 distributions such as AlmaLinux 8, CentOS Stream 8, Oracle Linux 8, Red Hat Enterprise Linux 8, and Rocky Linux 8. If you have the orcharhino Client synchronized, you can continue using it.
- We no longer maintain the orcharhino Client for Debian 9 due to the Debian project no longer providing any security updates. Please note that we offer orcharhino Clients for Debian 10 and Debian 11. If you have the orcharhino Client synchronized, you can continue using it.
Changelog Bugfixes
- Fixed a bug that caused PostgreSQL to show error messages all the time indicating that you need to do a systemctl daemon-reload because of the postgresql service.
- Fixed a bug that prevented the provisioning of EL8 using the minimal ISO image due to the missing dhclient package.
- Fixed bug that modulemd-defaults metadata were not copied to filtered CVs
- Fixed a bug which prevented creating snapshots using Foreman Ansible Modules if a snapshot with same name already existed.
- Fixed occasional issue during host-registration which resulted in Host-Registration failing with ‚HTTP error (404 – Not Found): Consumer with id e6ec3369-9568-4851-888c-75d08edf1624 could not be found‘
- Fixed a bug that in rare circumstances a Debian Errata was available twice and therefore the unique constraint was violated.
- Improved error message if reclaim disc-space option is used but no supported repository available (reclaim disc-space only works for ON_DEMAND repos)
- Updated rubygem-rack to fix CVE-2022-30122
- Fixed a bug causing missing architecture „all“ packages when syncing multiple Debian 11 distributions into a single repository.
- Fixed a bug preventing DEB repos from being visible to clients if they have multiple architectures set.
- Updated rubygem-tzinfo to fix CVE-2022-31163
- Assessed CVE-2022-42889 to be low impact for orcharhino (see https://atixservice.zendesk.com/hc/de/articles/6486350326812-CVE-2022-42889-Apache-Commons-Text-vulnerability)
- Updated ruby-on-rails to fix CVE-2021-22942, CVE-2021-44528, CVE-2022-21831, CVE-2022-23633, CVE-2022-32224, CVE-2023-22794
- Updated Django to fix CVE-2022-41323
- Fixed a bug in the Salt plug-in which mistakenly uploaded the same report twice: through the recurring cron job and the Salt reactor.
- Fixed a bug that only allowed certain characters for Content View labels.
- Fixed a bug in ACD plug-in that Ansible variables cannot be saved in orcharhino management UI.
- Fixed katello-tracer-upload not working after system reboot
- Fixed a bug that there is no description mentioning the added errata and DEB packages if an incremental CV is created because of errata installation.
- Fixed a bug that prevented to delete a host managed by a Microsoft Windows DNS server.
- Fixed a bug that prevented overwriting the „use installation media“ setting on the „Create Hosts“ page when using „Synced Content“.
- Fixed a bug Salt-plugin which could not handle Salt error report format
- Fixed incorrect timestamp for Ansible reports.
- Fixed a bug which prevented creating offline backups